Introduction
In the modern IT landscape it is important to know what cloud applications your users are using while also having the ability to block access to those apps if needed.
For that reason, Microsoft offers a Cloud Access Security Broker solution called Microsoft Defender for Cloud Apps (MDCA) as a part of their Microsoft Defender product line.
You can use MDCA to analyze cloud application usage of your users, sanction or unsanction those apps or control how your data can be used in those apps (depending on the implementation of the app into MDCA). You can also use MDCA to monitor complete sessions and control up- and downloads to those applications based on multiple criterias by connecting the apps to your Azure AD and leveraging Azure ADs Conditional Access policies.
The downside of connecting a cloud app in that way is, that through this the cloud application is automatically sanctioned in MDCA, but the sessions are only monitored if the users are logging in with their Azure AD credentials into the cloud app. If a user chooses to login with private credentials, the sessions are not monitored and it is not possible to control what data is shared within these sessions.
The recommended remediation to this issue is making sure to protect and encrypt your important and confidential data.
In this article however, I'm pursuing the goal to allowing access to a Azure AD connected Dropbox Business instance while blocking the ability to share data to private Dropbox accounts.
Products used
To achieve this goal, I'm using the following Microsoft products.
- Microsoft Defender for Cloud Apps (MDCA) (to monitor and control sessions to the connected Dropbox for Business instance)
- Microsoft Endpoint DLP (to limit upload and download possibilities to all other Dropbox instances)
Microsoft Defender for Cloud Apps: Connect Dropbox Business for Session Control
Connect Dropbox to AzureAD for SSO
First, we need to connect the Dropbox for Business instance to Azure AD for single sign-on.
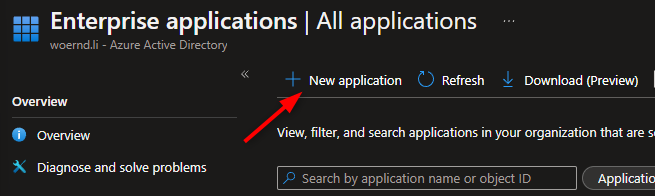
1. Go to the Enterprise applications blade in Azure AD and add a new application (Enterprise Applications)
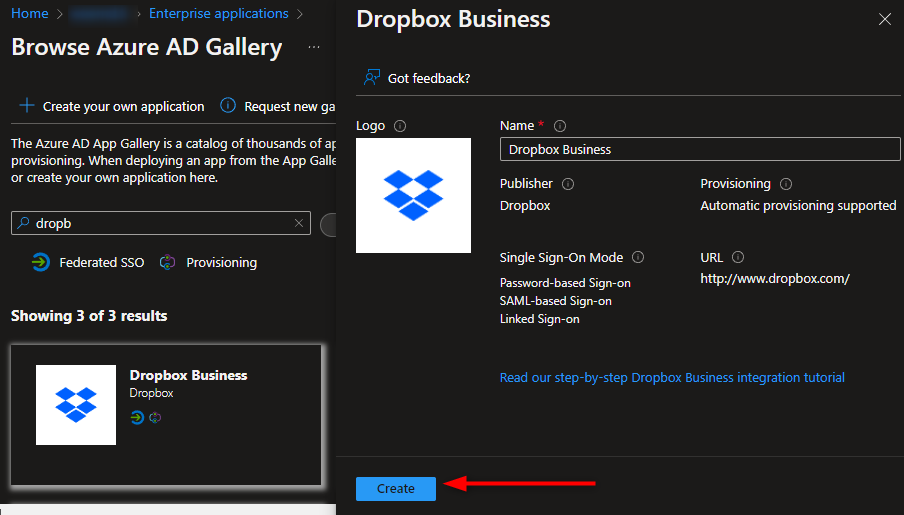
2. Search for Dropbox Business, select it and click Create
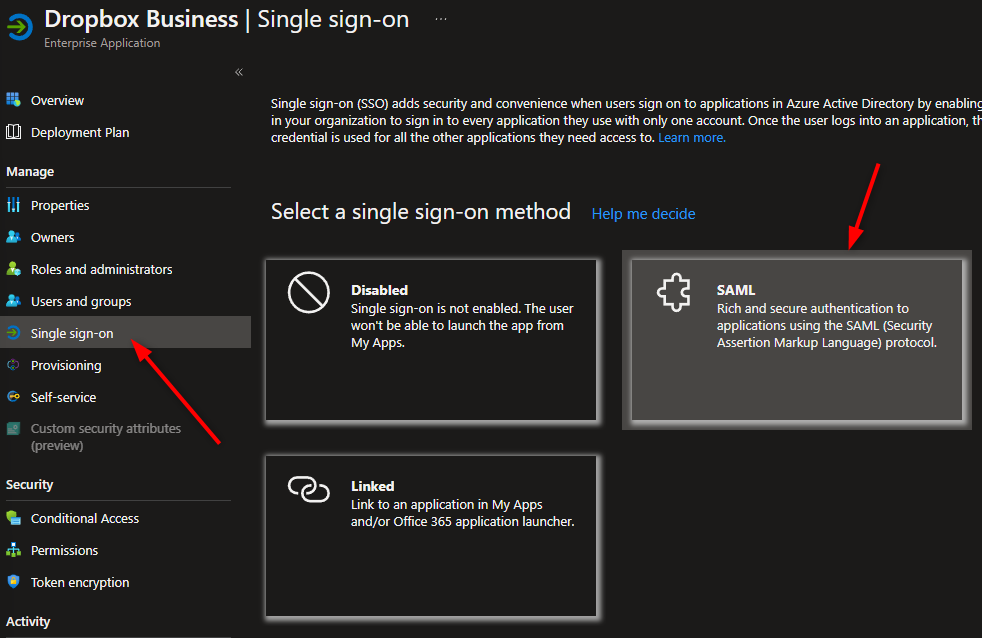
3. When the app is created, go to the Single sign-on blade and choose SAML
4. Edit the basic SAML Configuration
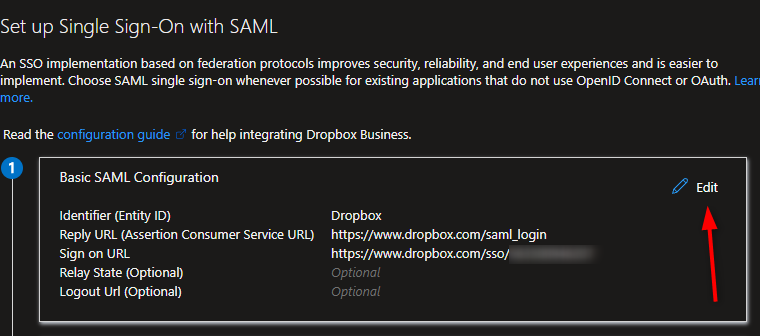
5. Add "https://www.dropbox.com/saml_login" as a Reply URL and add the Sign on URL which you can find in the Single sign-on configuration of your Dropbox Business account.
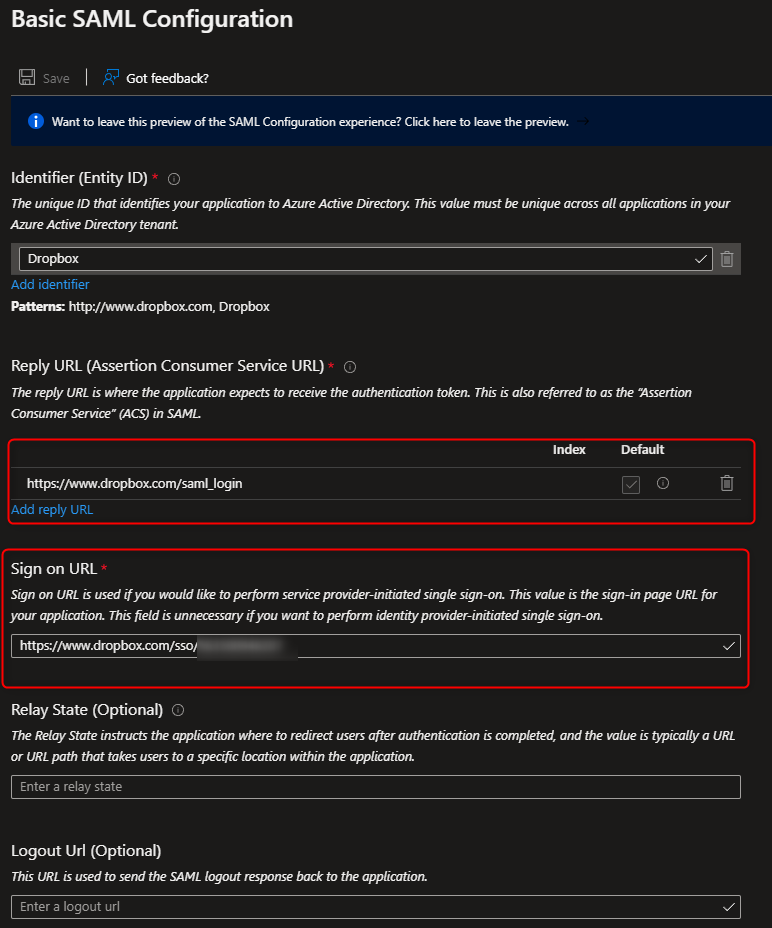
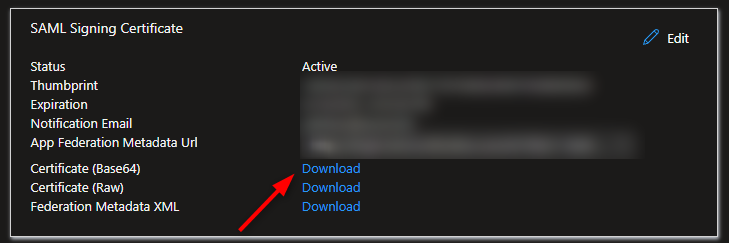
6. Download the SAML Signing Certificate and upload it in the SSO settings of your Dropbox Business account
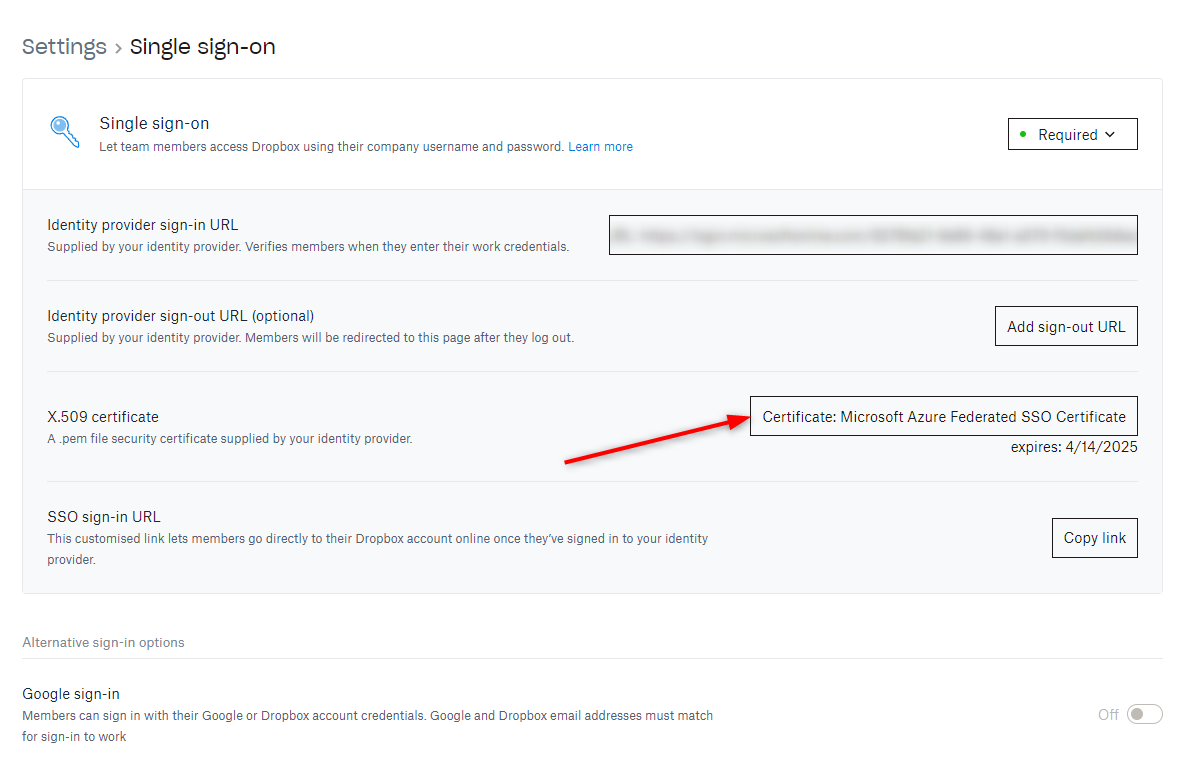
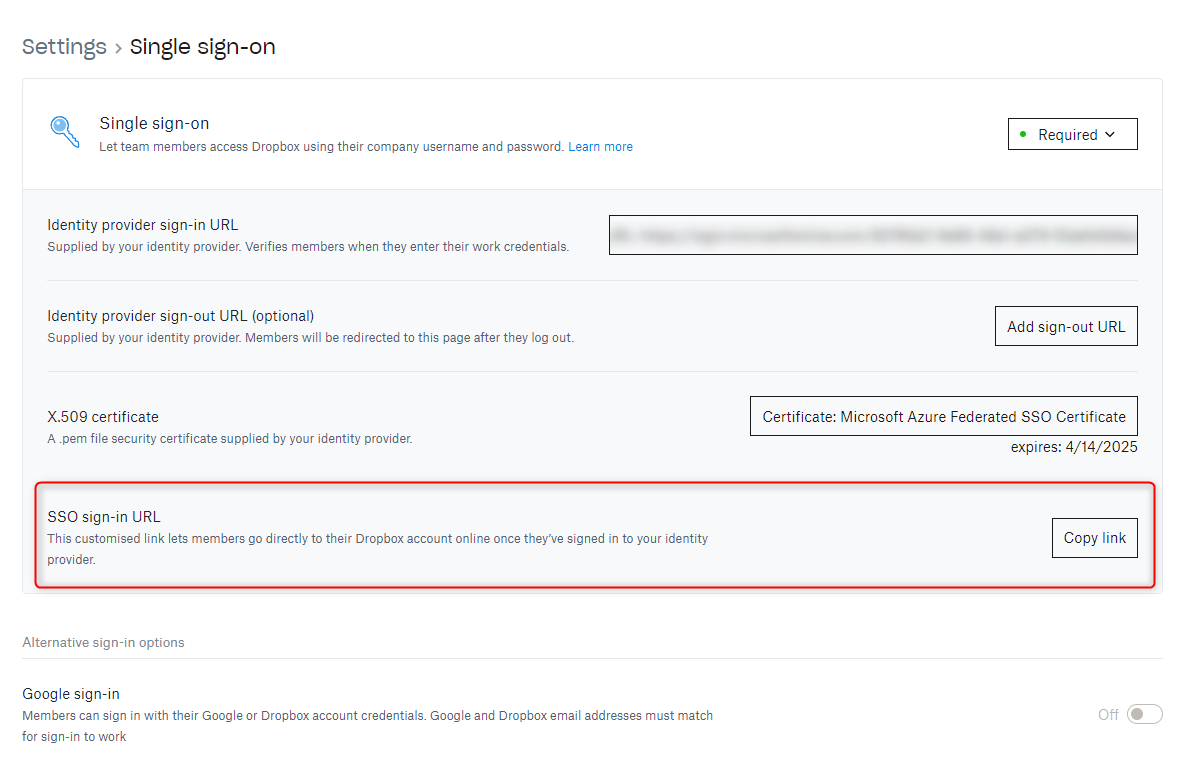
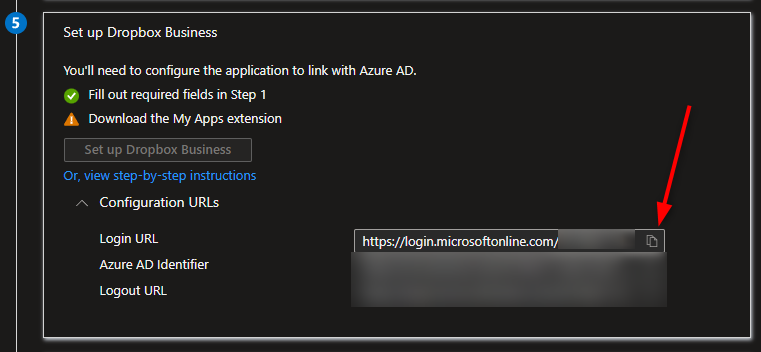
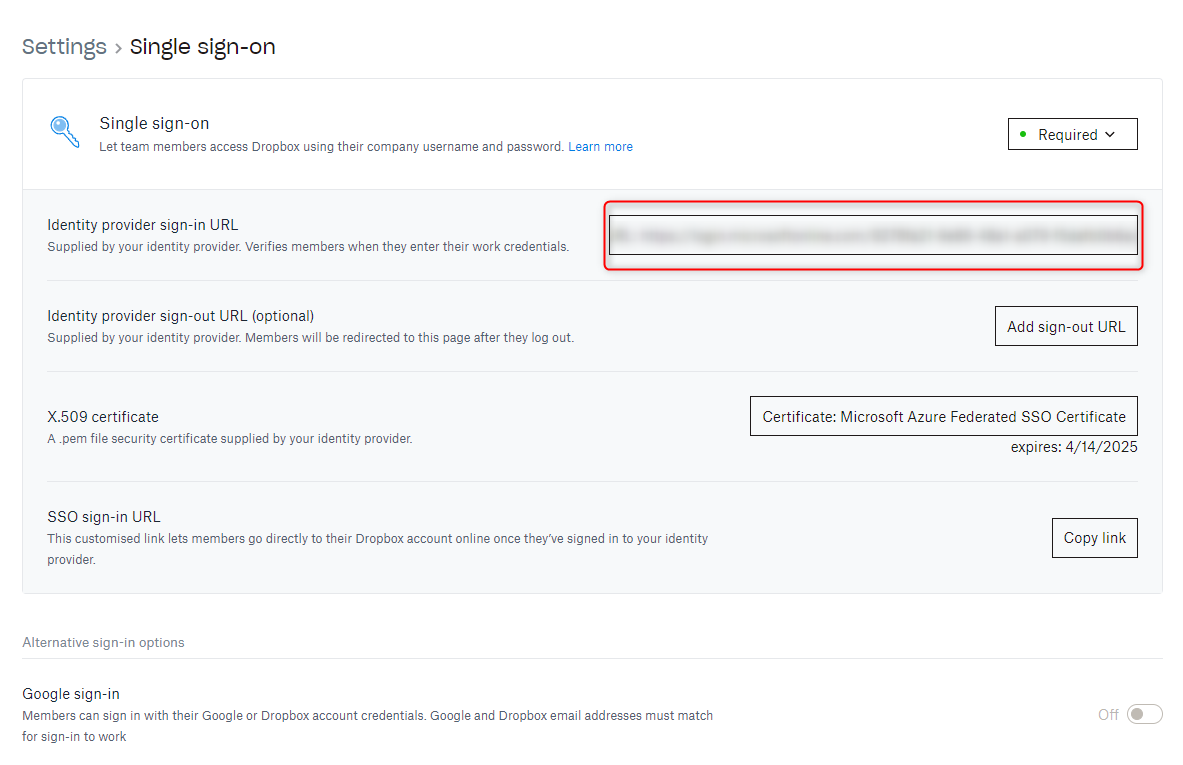
7. Copy the Login URL and add it as the Identity provider sign-in URL in the SSO settings of your Dropbox Business account.
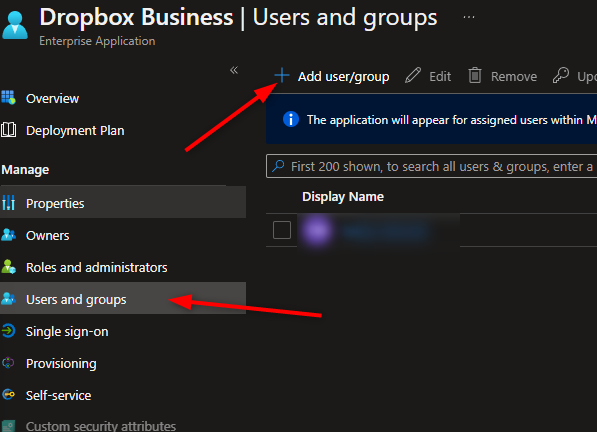
8. To finish the configuration, add the users or groups which will have access to this application
Create Conditional Access Session Control Policy
1. Go to Azure AD Conditional Access in the Azure Portal (Conditional Access - Microsoft Azure)
2. Create a new Policy called "CA001 - Dropbox Business Session Control"
3. Select users or groups to assign this policy to
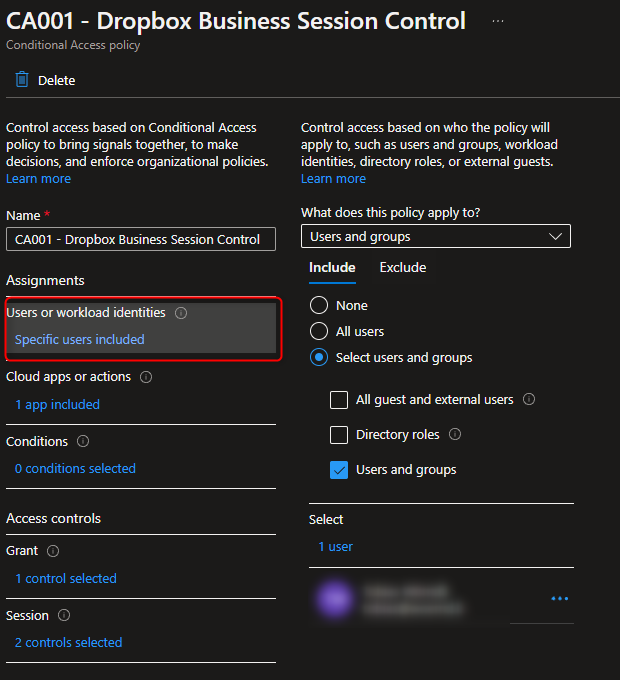
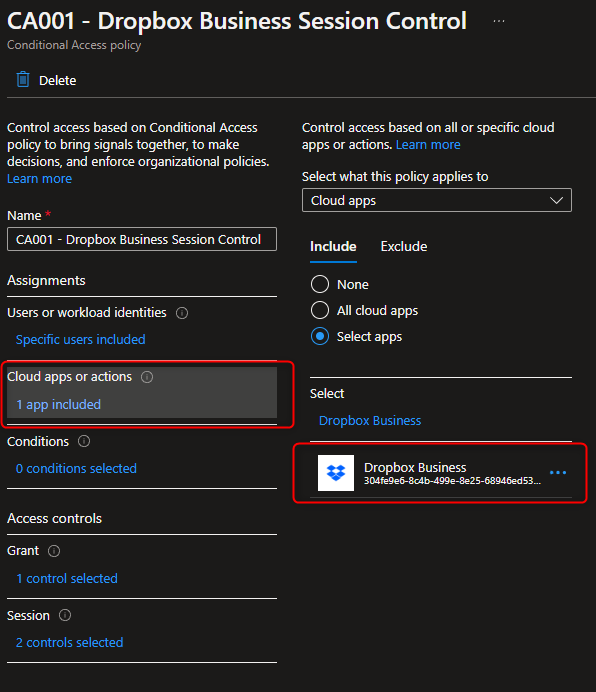
4. Selecct Dropbox Business
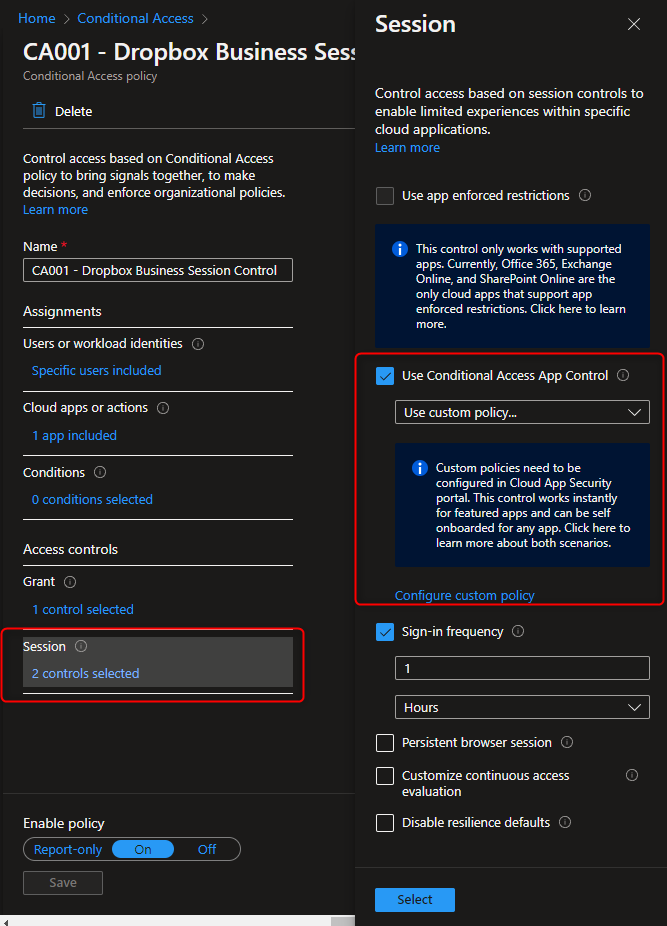
5. Choose "Use Conditional Access App Control" in Session Control and select "Use custom policy..."
Create Conditional Access Policy in Microsoft Defender for Cloud Apps
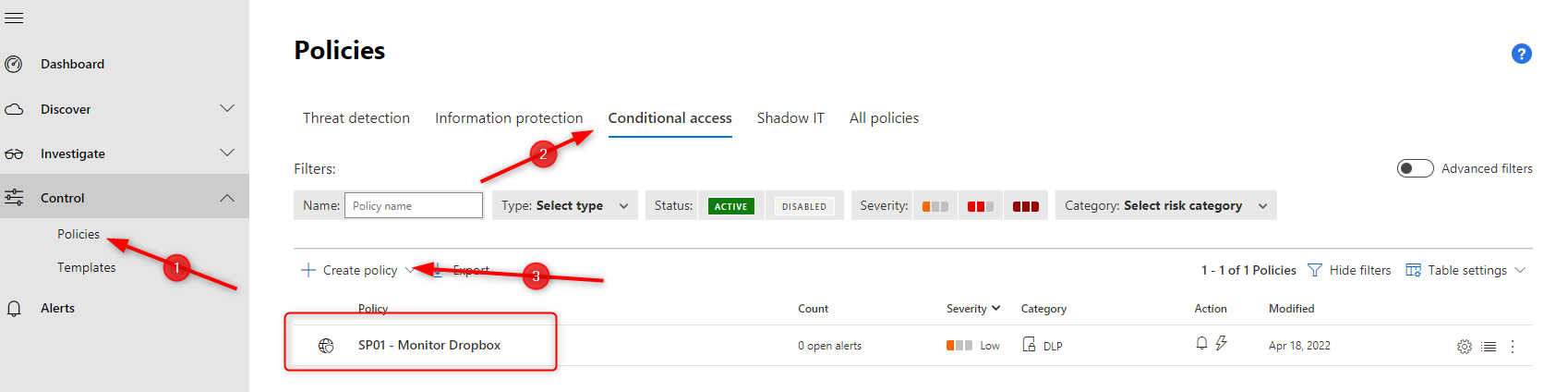
1. Go to the MDCA Portal
2. Navigate to Conditional access in Control -> Policies and create a new policy called: "SP01 - Monitor Dropbox"
3. Filter the Acitivity source to Dropbox
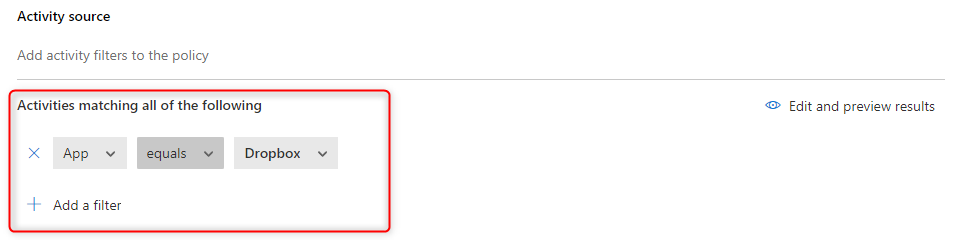
4. Set the session control type to Monitor only. Note: Here you can also control the the activities performed within your connected Dropbox instances, but this is not the scope of this article.
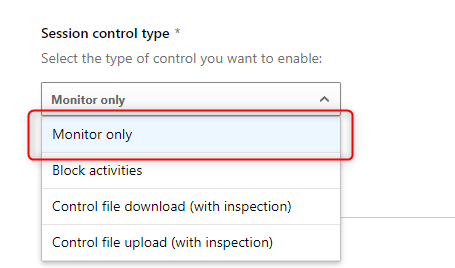
5. Save the policy
Result
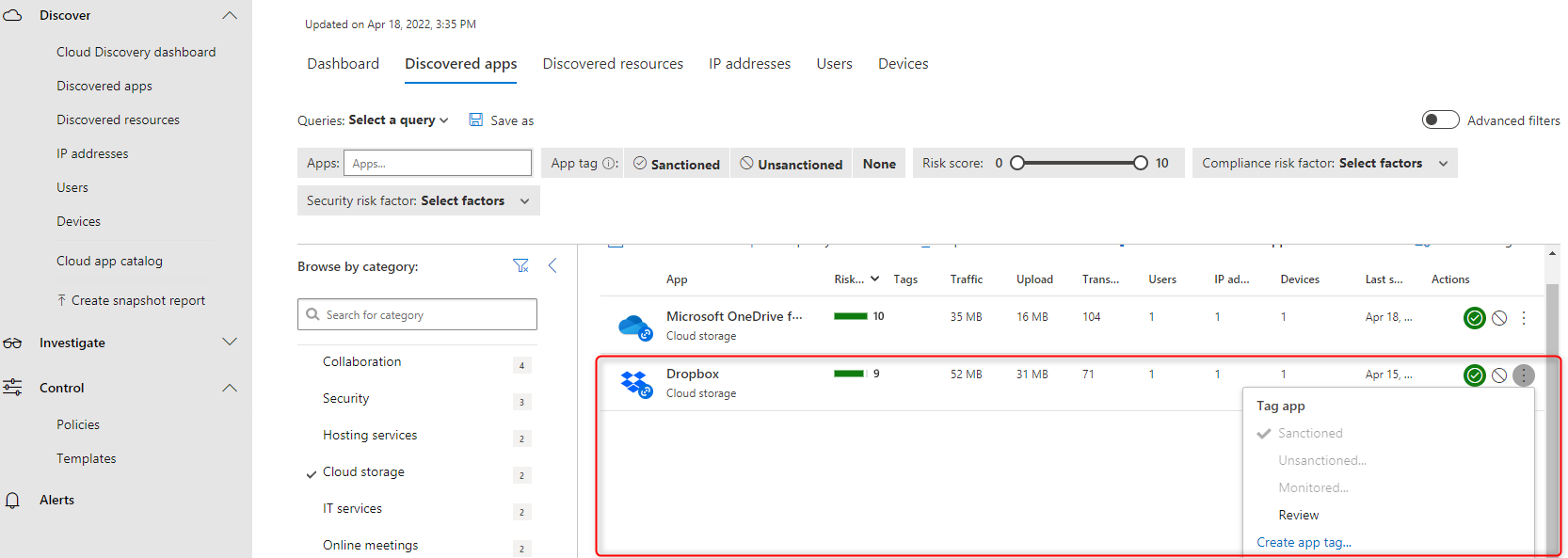
If we now navigate to Discovered Apps in MDCA portal, we see that Dropbox has been sanctioned as a cloud app and we cannot unsanction it as long as it is connected.
After logging into Dropbox with our Azure AD Credentials, we see that MDCA is redirecting our traffic through a reverse proxy to monitor the Dropbox traffic.
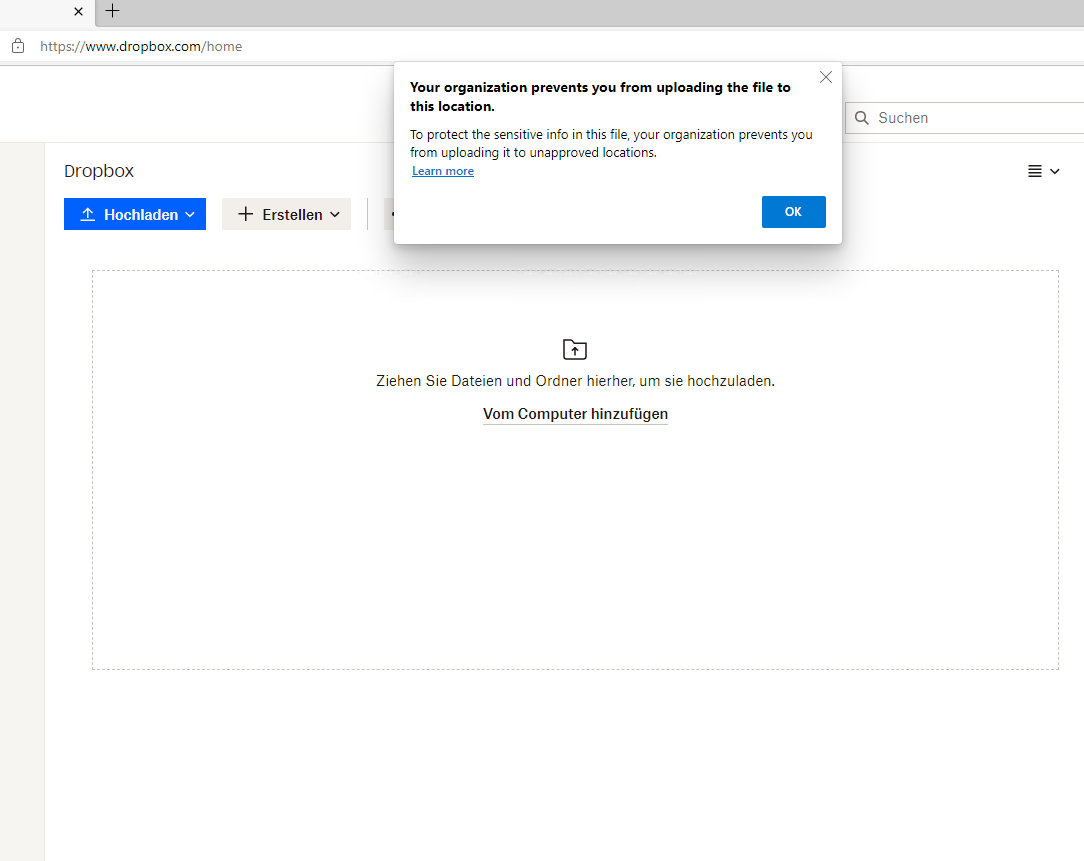
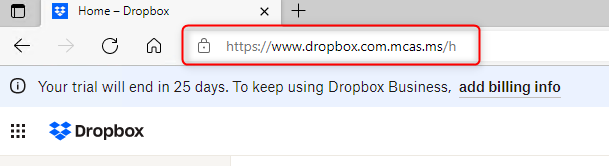 If we login with a private credentials to another Dropbox instance, traffic is still going directly to www.dropbox.com and cannot be controlled.
If we login with a private credentials to another Dropbox instance, traffic is still going directly to www.dropbox.com and cannot be controlled.
Microsoft Endpoint DLP: Limit Upload capabilities to Dropbox
Configure service domain restrictions
1. Go to the Microsoft Compliance Portal
2. Choose Endpoint DLP Settings in the Data loss prevention blade
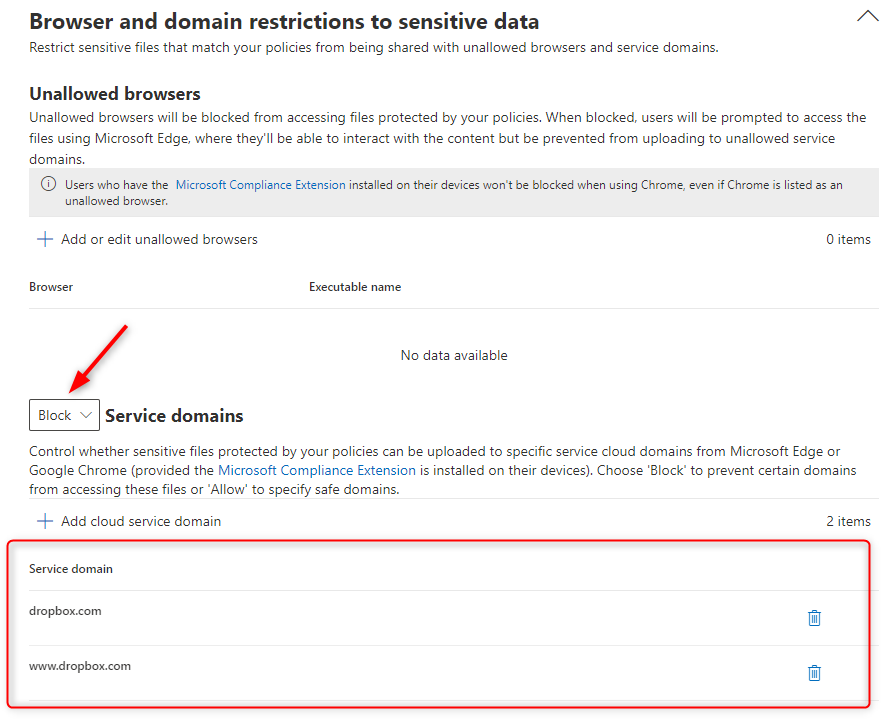
3. In "Browser and domain restrictions to sensitive data" choose "Block" for service domains and add the Dropbox domains. (In production you would change this to "Allow" service domains and only allow your explicitly sanctioned domains)
Create Data loss prevention policy
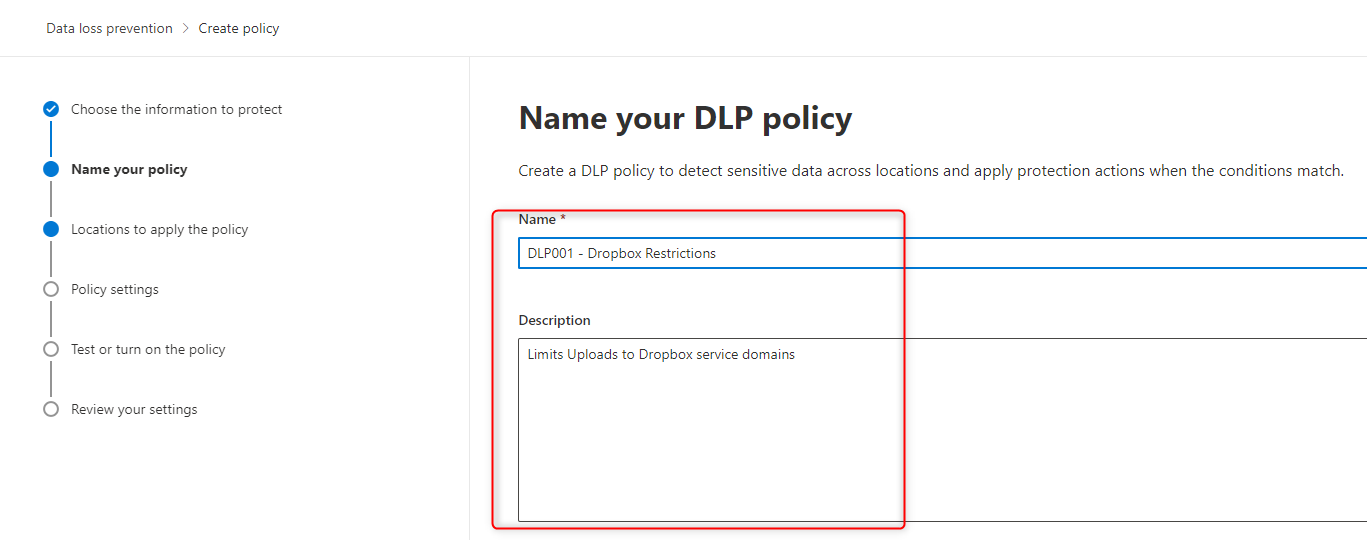
1. Create a new custom policy named DLP001 - Dropbox restrictions
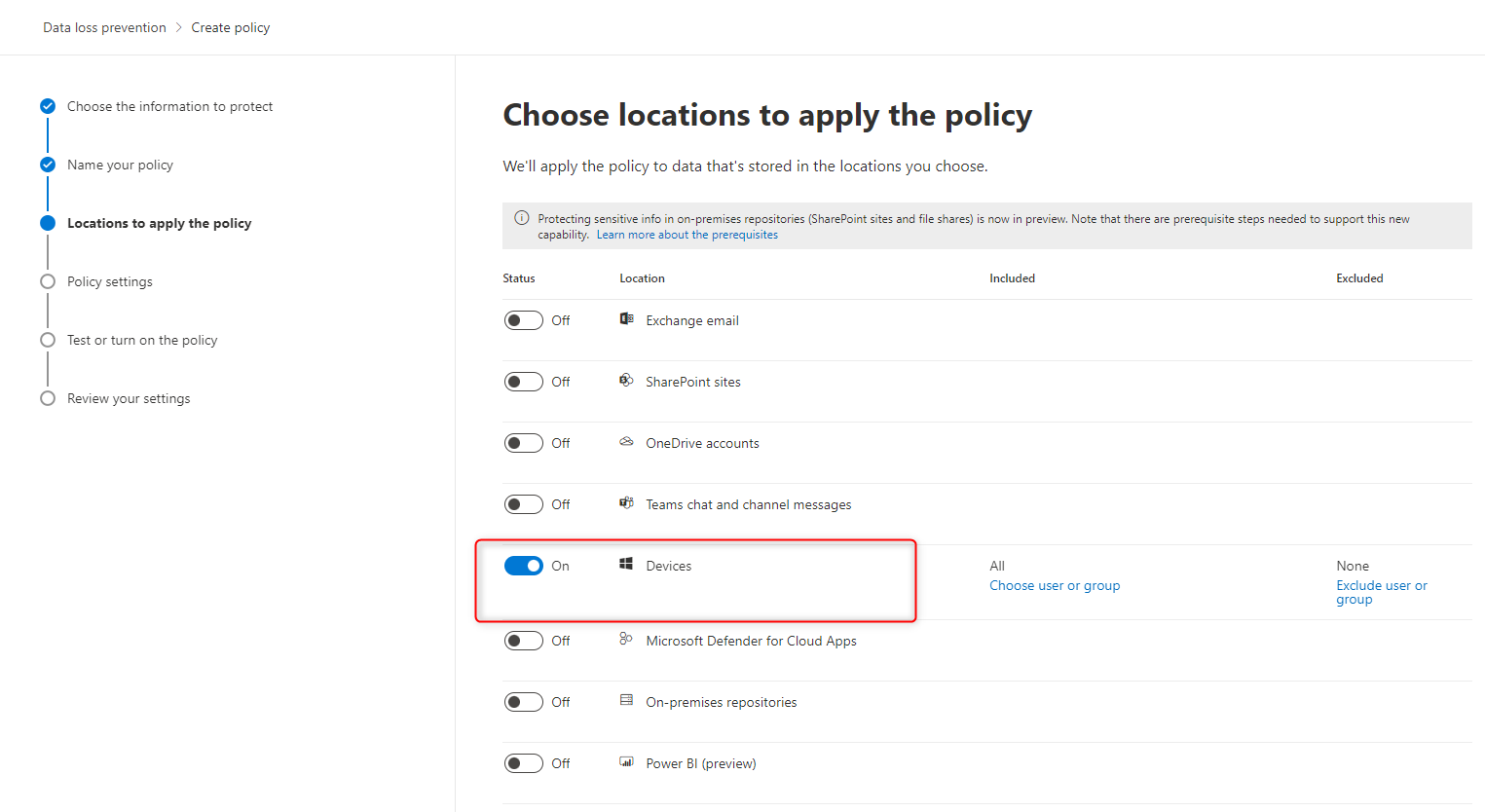
2. Apply the policy to Devices only
3. Create 2 custom rules: - DLPR001 - File Type -> Detects content to restrict by file type
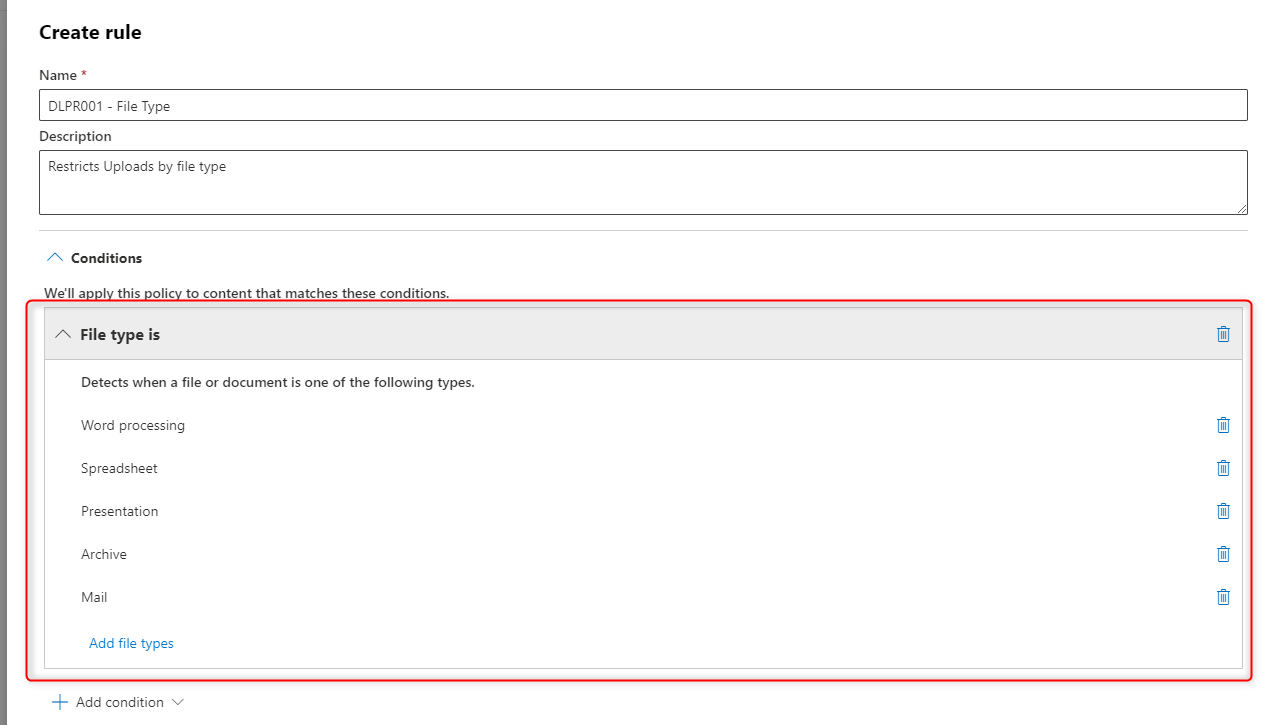
- DLPR002 - File extension -> Detects content to restrict by file extension
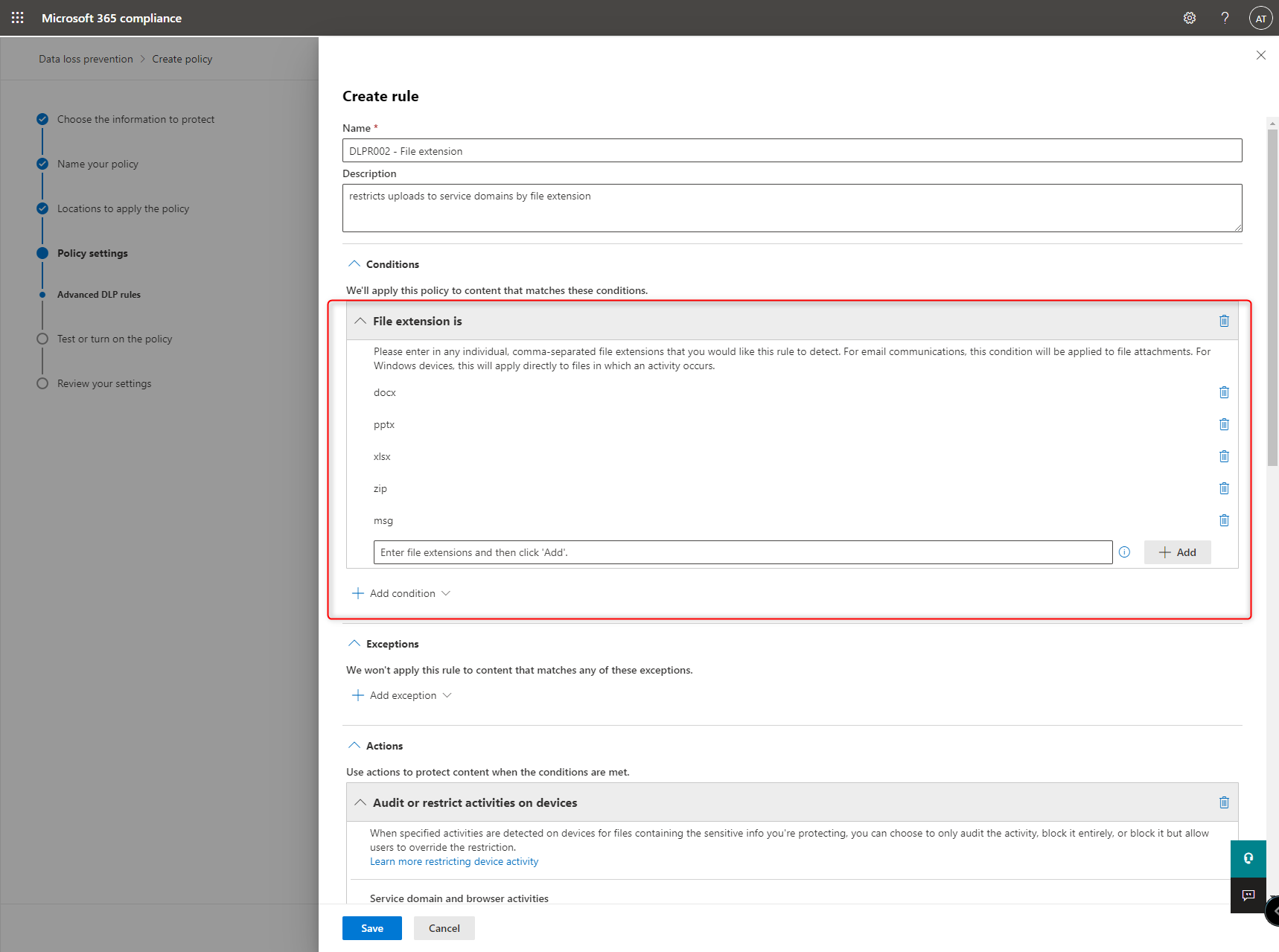
Block Service domain and browser activities for both of them:
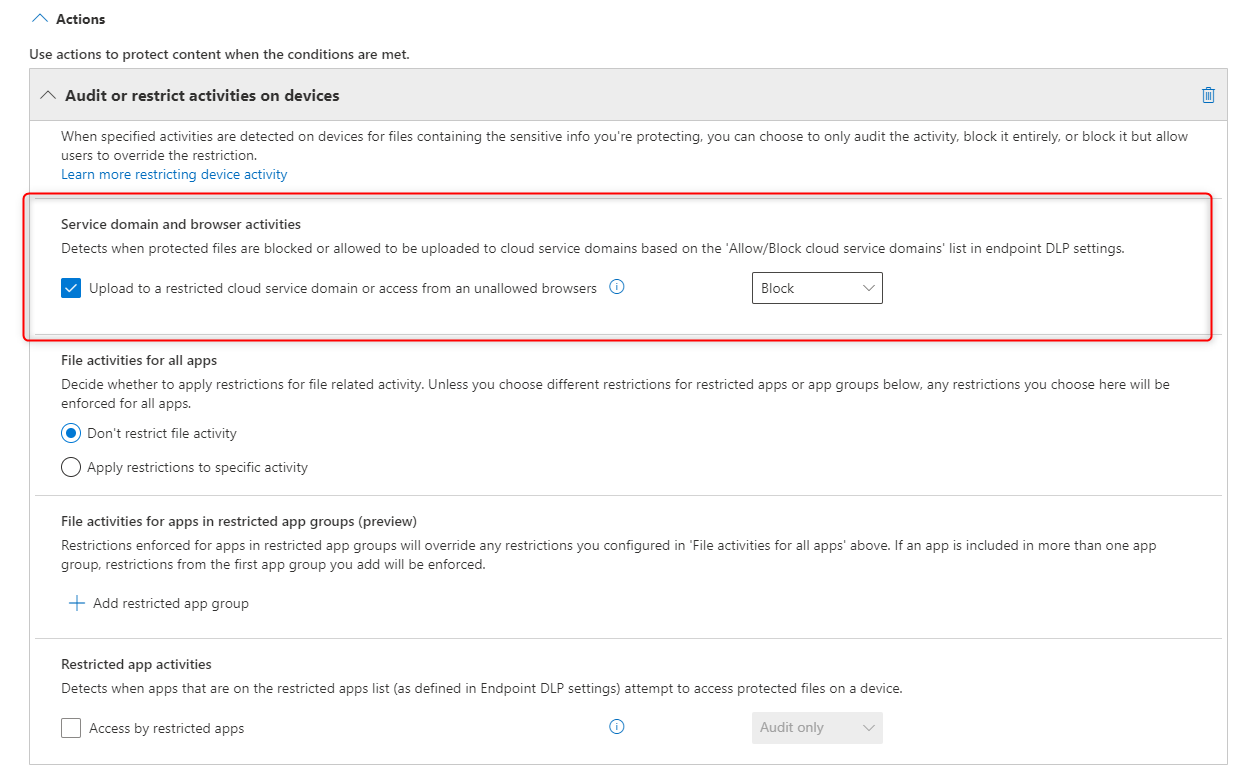
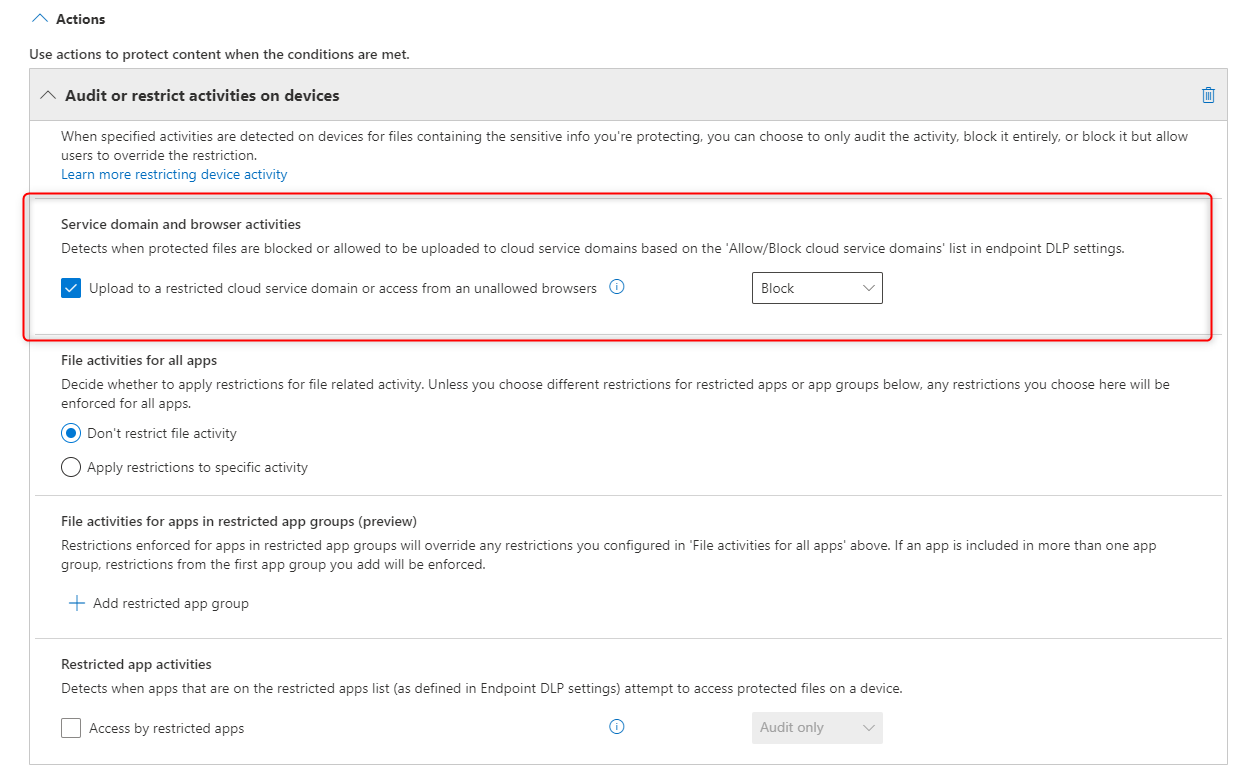
4. Save the policy and wait up to an hour for the new policy to become active.
Result
When logging in to our Dropbox business account, we can still upload documents
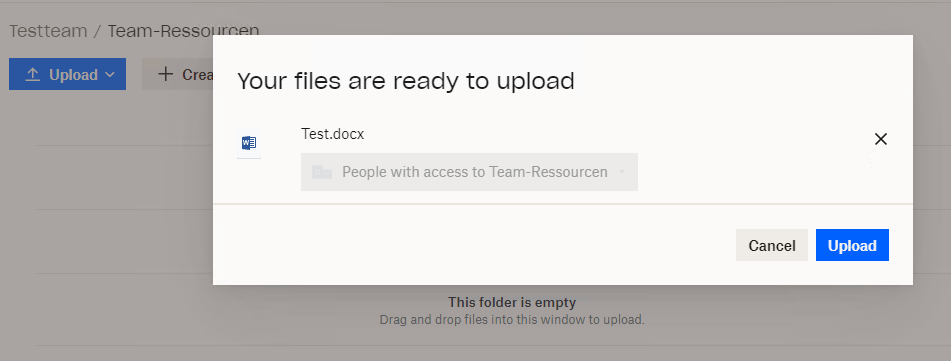
When logging in with a private Dropbox account, upload of documents is restricted based on the service domain.